In the previous article, we introduced what is the dark web and everything about it.For most people, accessing the dark web still has a certain threshold.Although can access dark web through some secure browsers such as Freenet and the Invisible Internet Project, but Tor is by far the most popular and straightforward way to access the dark web.In this article, we’ll look at what Tor is . Then, we’ll take a look at how tor browser works and how to install it .and how to access the dark web using tor browser.
What Is the Tor Browser ?
Tor is a program you can run on your computer that helps keep you safe on the Internet. It protects you by bouncing your communications around a distributed network of relays run by volunteers all around the world: it prevents somebody watching your Internet connection from learning what sites you visit, and it prevents the sites you visit from learning your physical location. This set of volunteer relays is called the Tor network.
You can still use Tor Browser to visit regular surface websites like YouTube and Wikipedia. However, unlike other browsers, Tor can also access hidden “.onion” sites found on the dark web.
How Does Tor Work?
To anonymize Internet usage, Tor routes traffic through multiple randomly-chosen relay servers before accessing the destination website. There are over 7,000 of these servers, which mostly belong to volunteers. The request is encrypted multiple times, so the relay servers only know the previous relay and the next relay, but not the request contents or the full circuit. The network request finally exits the Tor network at an exit node. From the website’s perspective, you are browsing directly from the exit node.
Tor hidden services, which will be covered below, are accessed in a slightly different way from standard websites — they use .onion domain names and are inaccessible from the regular web.
To actually use Tor to anonymize your communications, you run the Tor Browser on your computer. The Tor Browser is a modified version of Mozilla Firefox that connects to the internet via the Tor network. In addition to the functionality necessary to use Tor, the Tor Browser also bundles a number of extensions that help users maintain their privacy. For example, the NoScript extension is bundled with Tor out of the box, meaning that users have to manually approve individual JavaScript files before they can run—helping to protect against fingerprinting and browser security exploits.
Tor browser security
Using Tor Browser gives you a degree of security, but your traffic is only protected within the browser itself (not across your whole device). The websites you visit can’t see your IP address, and your ISP can’t see the specific sites you visit. However, your ISP can still see if you use Tor, which can flag suspicions — even if you’re not doing anything illegal. Plus, you’re not protected from malware, so downloading anything with Tor alone can be dangerous.
There’s also no way of telling who’s behind the nodes, or their intentions. Exit nodes can read, intercept, or alter your data. Even worse, malicious exit nodes can form a connection with your network — potentially allowing them to spy on all of your online activity. There have also been cases of bad actors (one in particular known as KAX17) who run malicious servers in entry, middle, and exit nodes to de-anonymize Tor users.
In terms of criminal activity, drugs, and disturbing images and videos: you’ll only find them if you want to — and even then, only if you know exactly where to look. If you think of the surface web as a mainland continent of interlinking sites, the deep web is more like a series of standalone islands. So you don’t really have to see anything you don’t want to see.
How to Install Tor Browser
I recommend only installing Tor Browser from its official website for safety purposes
System requirements
Tor Browser is based on Mozilla Firefox’s ESR (Extended Support Release), which periodically updates to include critical security updates from Firefox’s main version. Due to these updates, older operating systems may eventually become incompatibile with newer versions of software dependencies that are only available in more recent OS versions. Maintaining support for outdated systems would compromise the security of Tor Browser, as it would require disabling newer security features and mechanisms that are crucial for protecting users’ online anonymity.
Note: Support for Windows 7, 8, and 8.1 will be discontinued after the release of Tor Browser 14, scheduled for the end of 2024. Users on these operating systems are strongly advised to upgrade to maintain access to the most recent updates and security features provided by Tor Browser.
Windows
Operating Systems (32-bit and 64-bit):
- Windows 7
- Windows 8 and 8.1
- Windows 10
- Windows 11
macOS
- macOS 10.12 and later.
Linux
Tor Browser is supported on any modern Linux-based operating system. Please reach out if you encounter any issues while installing.
Android
- Android 5.0 or newer.
Installation
The process of setting up Tor on Windows and Mac is largely alike, with the only variations being in the way you interact with the respective operating systems. Below are the instructions for installing Tor on a Windows machine.
1.Download Tor. Go to the download page and select the appropriate installer
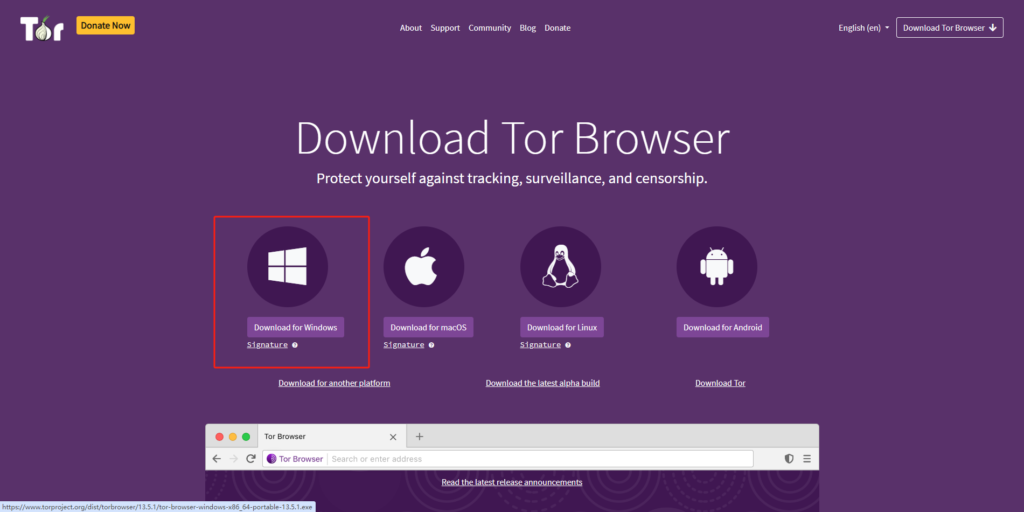
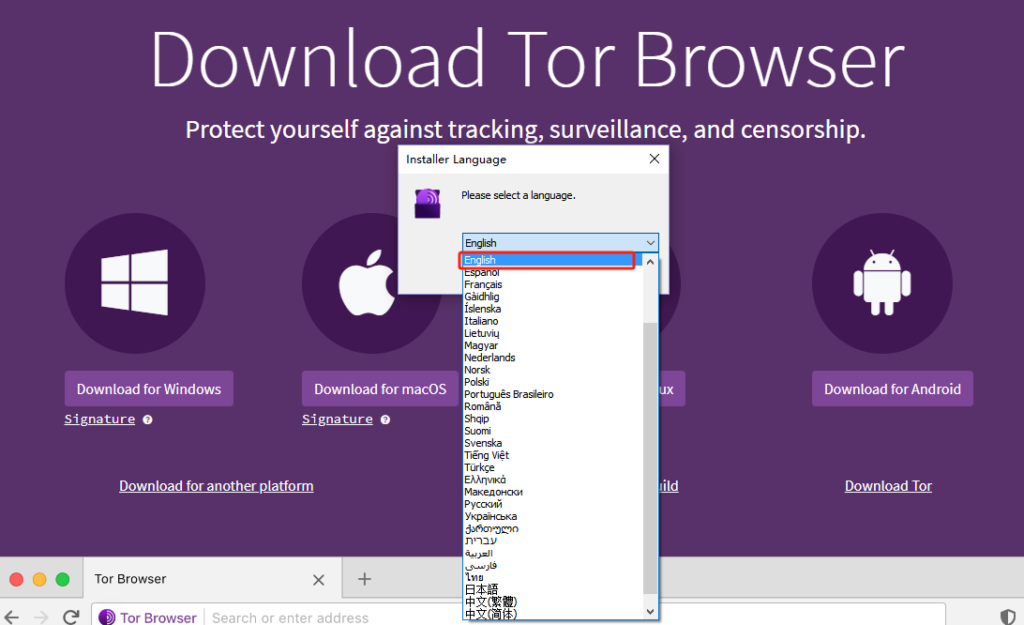
2.Open the installation file. Pick a language and follow the installation wizard
3.Connect or configure Tor. If you’re browsing in a restrictive network or location, click Configure connection. It will ask you if Tor is censored in your location or if you’re using a proxy — then it will help you configure a pluggable transport.
Once the connection is successful, open the Tor browser. You should now be able to browse hidden “.onion” sites found on the dark web using Tor.
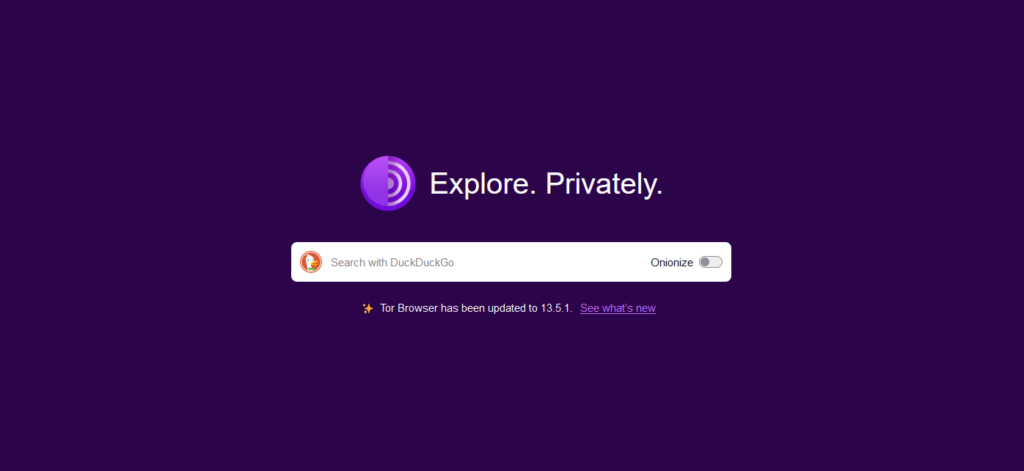
What should be considered when accessing the dark web?
be cautious about what you download or do on the dark web – everyone is more or less anonymous there, so there is little accountability.
If a user or website you trust turns out to be malevolent and attacks you, you won’t have many options for getting help
On the other hand, using the dark web can be safer for whistleblowers, journalists, or dissidents whose communications are being monitored by governments or other organizations. It depends on who you are, what you’re doing, and how tech savvy you are.
Our general recommendation is to steer clear of it.